In the version 2.7.4, the biggest update should be the flexibility of message blocker scope. As the picture shows, you can see you can add many rules about what kind of message you want to intercept.
Certainly, you will also be able to check and tamper the data on the fly using this feature. The scope is defined by three ones:
- SERVER: FROM SERVER TO CLIENT
- PROXY: FROM INITIATOR TO RECEIVER
- PROXY: FROM RECEIVER TO INITIATOR
The TCP server currently provides two service:
- HTTP server
- HTTP proxy server
HTTP server scheme:
- HTTP server(PentestSuite) --> Client
- HTTP server(PentestSuite) <-- Client
In the scheme of HTTP server, SERVER: FROM SERVER TO CLIENT means the data that will be sent to client, which is the first in the HTTP server scheme.
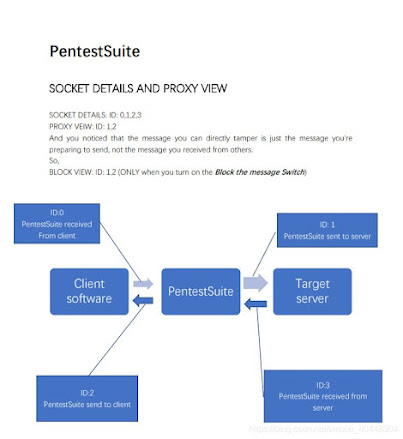
HTTP proxy server scheme:
According to the picture...- PROXY: FROM INITIATOR TO RECEIVER means id 1;
- PROXY: FROM RECEIVER TO INITIATOR means id 2.
You can also specify the keyword that you want to match in the data, leave it blank if you want to intercept everything in scope.
You can add, change, delete, append any rules you want by two buttons. PentestSuite will make sure every message will be checked if it match the specified rules.
Every change of the rule you will need to make the decision whether you want to drop or forward all the messages. You can specify this by a switch with name: FORWARD UNSENT MESSAGE(S) AFTER SETTING.
Thanks for your reading and that's the main update for the version 2.7.4 of PentestSuite.


Comments
Post a Comment